Malware and malvertising continues to infiltrate mobile app inventory, disrupting the user experience, hurting retention, and putting monetization at risk. As unsavory advertisers deploy malicious creatives through programmatic channels, mobile publishers and game studios are facing real business consequences: low ratings, user churn, and App Store complaints.
In this guide, we break down how malware campaigns and malvertising vectors enter your app via programmatic demand partners and how to operationalize real-time ad quality protection across your app. With AppHarbr’s expertise in mobile malvertising defense and in-app ad quality enforcement, you’ll gain a playbook for identifying, blocking, and staying ahead of malware threats reclaiming control over both your revenue and your reputation.
What Are Mobile Malware Ads and Why Should Developers Care?
Mobile malicious payload ads are seemingly ordinary advertisements that conceal harmful code and cyber threats. These malicious ads exploit vulnerabilities, causing significant damage to business revenue, retention, and brand reputation. Understanding the nature of mobile malvertising is vital to business interests, monetization models, and ensuring app longevity.
Malicious ads on mobile devices often appear indistinguishable from legitimate creatives, making detection particularly challenging for publishers and their ad operations teams. These campaigns are thoughtfully designed to bypass basic monitoring and scanning procedures, resulting in widespread distribution across apps prior to detection. Developers must understand that a single malvertising incident can severely undermine user trust, negatively affect app ratings, disrupt monetization efforts, and potentially lead to regulatory penalties and costly remediation efforts.
Therefore, mobile publishers require proactive, specialized knowledge and robust technology solutions to accurately identify and eliminate malicious creatives before they’re served. Prioritizing the prevention of security attacks not only secures revenue streams but also reinforces brand trust, ensures compliance with privacy regulations, and promotes a secure monetization ecosystem.
How Do Mobile Ads Deliver Malware to Users’ Devices?
Malicious advertisements deliver malware through hidden scripts and payloads embedded in creatives and landing pages. Scammers have a few main strategies for using advertising to make money. They infect users with malicious payloads that harvest their financial data for use or sale on the dark web. Similarly, they may infect users or make users think they’ve been infected with ransomware, forcing users to pay for their stolen files back. Attackers also trick users into paying for a false product, when the scammers then collect the money with no product in return. This scam is typically limited to a one-time payment, but if a scammer acquires a user’s bank details or credit card information, they’ll drain the bank account. Such methods expose potential victims to security vulnerabilities, damage trust, undermine retention, and ultimately impact your revenue.
Malicious ads deliver malware via:
- Embedded JavaScript that executes pre and post click
- Redirect chains that hijack user sessions
- Landing pages with exploit kits or fake app downloads
Recognizing Mobile Malvertising: Symptoms and Warning Signs
Most malvertising campaigns are designed to run quietly, making detection difficult. Still, there are warning signs. Malvertising often enters app environments through programmatic channels, disguising itself within otherwise legitimate ad tags. Early warning signs include unsolicited app redirects, fraudulent pop-ups, intrusive permission prompts, and suspicious JavaScript or tracking scripts embedded in creatives or landing pages.
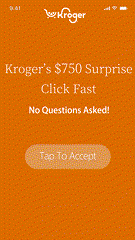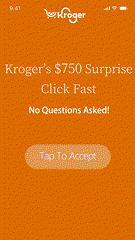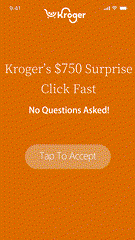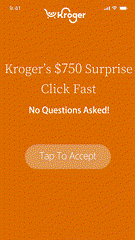
For publishers, these threats result in measurable operational impact: user churn, revenue loss, data exposure, regulatory risk, and elevated support costs. Continuous ad flow monitoring is essential but reactive detection alone isn’t enough.
Ad ops teams should also track behavioral anomalies such as spikes in user complaints about ad behavior, unusual traffic patterns tied to specific demand sources, and increased bounce rates or retention dips. These signals often indicate undetected malware activity already in rotation.
Preventing malvertising campaigns requires an in-app layer of protection. AppHarbr’s lightweight SDK blocks malicious payloads in real time before the creative is rendered. By filtering bad ads pre-bid, publishers maintain control over monetization quality, reduce operational strain, and protect users without relying on mediation or demand partners to act.
Malicious Payloads and Tracking Scripts in Ad Creatives
Programmatic pipelines, by design, introduce risk. The open exchange of third-party creatives, coupled with fragmented SDK integrations and inconsistent enforcement across networks, creates ample surface area for malicious payloads to slip through. Threat actors exploit verification blind spots—especially in mobile—where vetting is often deferred or outsourced. Manual QA and mediation filters aren’t built for this scale or sophistication. To maintain inventory integrity, publishers need purpose-built, in-app ad quality enforcement that operates in real time. Solutions like AppHarbr close the operational gaps left by programmatic fragmentation before a creative ever renders. This is the only way to securely protect against malicious behavior and attacks including:
| Auto Redirect | Automatically redirects users to another site or app without interaction |
| Button Hijack | Manipulating the back button to keep a user locked into a certain page |
| Brand Impersonation | Ads that imitate known brands to trick users into clicking or submitting data. |
| Deceptive Site | Directs users to sites designed to look legitimate while stealing data or pushing scams. |
| Fake Antivirus & Cleaners | Ads promoting fraudulent system scans or cleaner tools to scare users into action. |
| Fake Software Update | Prompts users to download fake or malicious software under the guise of an update. |
| Financial Scam | Ads promoting fake investment opportunities or money schemes. |
| Forced Browser Notifications | Tricks users into enabling browser notifications, often used for future spam or malvertising. |
| Gift Card Scam | Ads claiming users have won or can earn gift cards—used to collect data or install malware. |
| Landing Page File Download | Automatically triggers a file download without user intent on ad click. |
| Malicious Ad Post Click | Malware or scam triggers after user clicks the ad and lands on the destination. |
| Malicious Ad Pre Click | Malicious code embedded directly into the ad before any user click. |
| Malicious Extensions & Add-ons | Ads promoting browser extensions that hijack data, redirect traffic, or inject ads. |
| Malware Ad Post Click | Delivery of malware after ad click, often through scripts or downloads. |
| Malware Ad Pre Click | Ad itself includes or attempts to execute malware before interaction. |
| Malware Phishing | Ads that combine phishing and malware—stealing data while installing harmful software. |
| Misleading Product Offer | Ads for products with deceptive pricing, false promises, or fake endorsements. |
| Suspicious VPN | Ads promoting VPNs with hidden surveillance, malware, or shady affiliations. |
| Tech Support Scam | Ads impersonating tech support to convince users their device is infected or broken. |
Tools and Tactics to Block and Remove Malicious Adware on Mobile
Combining real-time ad security solutions with mobile-first ad quality platforms gives publishers a strong defense against malvertising. AppHarbr’s technology detects and blocks malicious creatives with precision protecting brand reputation and stabilizing monetization. Key strategies include real-time malware detection, strict creative screening, transparent partner vetting, and proactive threat intel.
Secure Your Apps and Revenue from Mobile Malware Ads
Malicious creatives remain a persistent and growing threat for mobile app publishers and developers. Effectively addressing these risks demands a proactive, multi-layered strategy combining real-time ad quality monitoring, rigorous partner vetting, and advanced malvertising detection tools. By adopting these best practices and partnering with specialists like AppHarbr, publishers can protect their monetization pipelines, preserve user trust, and keep up with regulatory requirements.
Don’t wait for a malicious ad to damage your app or your audience. Act now to secure long-term growth and safeguard your reputation with AppHarbr.




